A new type of ransomware called “Cheers,” Linux-based ransomware that targets the VMware ESXi platform, has recently emerged in the cybercrime space.
VMware ESXi is a popular virtualization platform used by enterprise users worldwide, and because of its widespread use, VMware ESXi has been a popular target for cybercriminal groups, with several groups recently targeting VMware, including the notorious LockBit, Hive, RansomEXX and RansomX. Hive, RansomEXX and others.
When Cheers attacks VMware ESXi servers, it launches an encryptor that automatically enumerates running virtual machines and shuts them down using the following esxcli command.
When encrypting files, Cheers specifically looks for files with the extensions .log, .vmdk, .vmem, .vswp, and .vmsn associated with ESXi snapshots, log files, swap files, page files, and virtual disks, each with the “.Cheers” suffix, and since file renaming occurs before encryption, if access to the renamed file is denied encryption will fail, but the files will still be renamed.
esxcli vm process kill –type=force –world-id=$(esxcli vm process list|grep ‘World ID’|awk ‘{print $3}’)
Cheers obtains the secret key (SOSEMANUK) from a pair of ECDH public and private keys held by Linux’s /dev/urandom and embeds it in the encrypted file. Since the generated private key is erased, decryption can only be achieved by relying on the private key of the ransom gang.
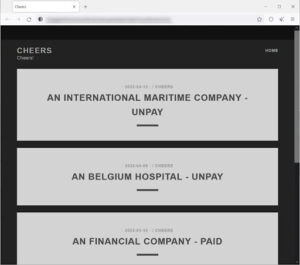
Meanwhile, Cheers creates a ransom note in each folder called “how to recover your files.txt”, which includes details of the victim’s encrypted files, links to Tor data breach sites, and ransom payment sites. The Onion website currently lists four victim companies and only has three days to negotiate a ransom payment or the victim companies’ data will be sold.
Although only the Linux ransomware version of Cheers has been found so far, variants targeting Windows systems cannot be ruled out as well, and VMware ESXi users need to take effective countermeasures against ransomware attacks as soon as possible.
How can VMware ESXi users protect themselves from ransomware?
Since it is difficult to completely avoid ransomware attacks, it is best to use backups to keep your data safe. CloudStart has a virtual machine backup solution for VMware that enables comprehensive data protection of VMware cloud architecture platform and reaches into the application system, effectively securing the data center from backup and recovery.
1. Multiple functions to enhance backup efficiency
Intelligent backup strategy, four backup modes: full backup, incremental backup, differential backup, and permanent incremental backup, and five-time strategies: daily, weekly, monthly, rolling, and one-time; meanwhile, backup can be achieved without installing any agent plug-in, effectively reducing operation and maintenance costs; deep and effective data extraction and deduplicated data compression functions, effectively saving storage space; LAN-Free transfer mode Improve LAN-Free transmission mode improves transmission efficiency and has minimal impact on production business systems.
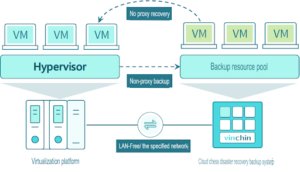
2. Instant recovery to ensure data security
CloudKi performs secondary recovery of VMware virtual machines and their data at the point in time of backup. The entire process has no impact on the original backup data, minimizing the occurrence of core business interruptions due to disasters or failures, effectively securing the original backup data, and laying the foundation for backup data validation.
3. Unique Backup Anti-Ransomware Features
Vinchin provides backup data encryption protection for virtual server backup solutions, encrypting backup data through bank-level algorithms. The unique Vinchin encrypted backup technology also monitors and protects backup data throughout its lifecycle. When ransomware or malware attempts to modify backup data, access is denied outright, providing additional protection for user data security.
4. Dual Protection for Offsite Disaster Recovery
Having a business-critical backup copy is critical to ensure that data can be recovered in the event of backup data loss. Transferring data that has been backed up locally to an offsite backup system and saving it as an offsite copy can effectively prevent data loss in the event of an overall disaster in the local data center.
We recommend that all VMware users put instant vm recovery on their schedule as soon as possible to ensure data security and not give cybercrime a chance to take advantage of it. Click here for a 60-day-free-trial.

